MetaCTF
One of the reasons to learn assembly code and binary executable
formats is to reverse-engineer unknown, potentially malicious,
software. MetaCTF is an experimental, metamorphic,
capture-the-flag game that is intended to teach concepts in this
course in a more interesting and fun manner. It consists of a
set of Linux/ELF binaries that are unique to each student. For each
binary, you are seeking an input that will force the binary to print
out "Good Job". Instructions are given for each binary when
they are run in order to guide you. You are to submit
your "winning" inputs that solve your binaries via the web site as
shown below.
Your binaries
- Each user has a set of binaries (and some source files)
located at the following URL
- https://cs201.oregonctf.org
- To login, your username is your Odin ID and your password
is the last 4 digits of your PSU student ID.
- Please let me know immediately if you can not log in
- To download all binaries from a linuxlab shell:
- mkdir A0
- cd A0
- virtualenv env
- source env/bin/activate
- pip install requests bs4
- wget http://thefengs.com/wuchang/courses/cs201/meta_dl.py
- python meta_dl.py cs201.oregonctf.org username password
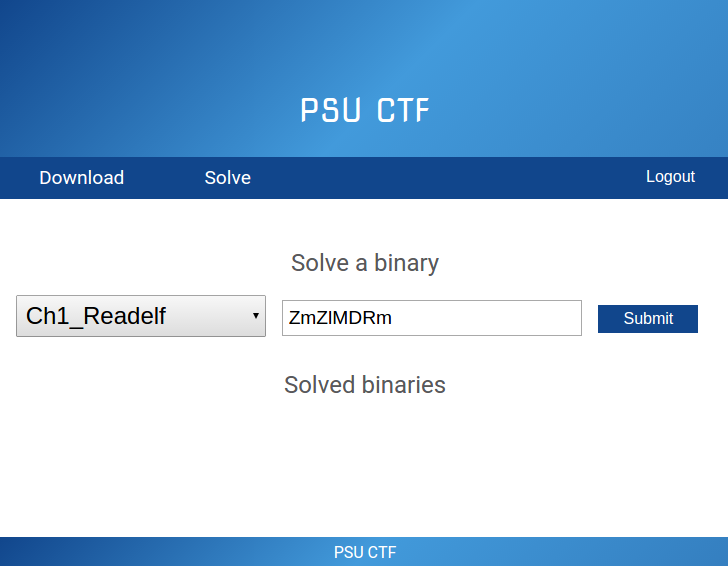
- Once logged in, there will be two options: Download and
Solve
- Use the Download link to get a zip file of your binaries
- Use the Solve link to submit individual answers to each binary
Example session
mashimaro <x/wuchang> %
ls
Ch1_Ltrace
Ch3_05_XorEnc
Ch3_09_HijackPLT
Ch1_Readelf
Ch3_06_SwitchTable Ch3_09_HijackPLT.c
Ch2_01_AsciiInstr Ch3_06_SwitchTable.s
Ch3_10_Structs
Ch2_03_XorInt
Ch3_07_StackSmash Ch3_10_Structs.c
Ch2_05_FloatConvert Ch3_07_StaticInt
Ch3_04_FnPointer Ch3_07_StaticStrcmp
mashimaro <wuchang> % ./Ch1_Readelf
In this level, you will experiment with basic static analysis of
binaries.
Your goal is to find the password that unlocks the program so it
prints
"Good Job". While you can solve this level many ways, try
using the
"readelf -a <binary>" to find the section number where the
password might
be stored, then use "readelf -x <section_number>
<binary>" to list the
contents of the section which likely has the password in it.
You may also
use the command "objdump -j" on the appropriate section of the
binary to
solve it.
Enter the password: ZmZlMDRm
Good Job.
mashimaro <wuchang> %
Example
screenshot